Basic API Authentication w/ TLS
There are no advanced options for using this protocol, so you are just sending a username and password that is Base64 encoded. Basic authentication should never be used without TLS (formerly known as SSL) encryption because the username and password combination can be easily decoded otherwise.Can be passed in either the headers or body when using SSl/TLS as both are encrypted
API Keys v’s username/password
Less secure, reused across many sites, they’re much easier to intercept, then compromised for all sites.API Keys have secrets that are securely randomly generated character strings over 40 characters long and have significantly greater entropy and are much harder for attackers to compromise.
API Keys are independent of the account’s master credentials, can be revoked and created at will – many API Keys can be granted to a single account. valuable for key rotation strategies, i.e. requiring a new key per month, or removing keys if you think one might have been compromised.
API Keys, because of their additional security (used with secure authentication schemes like digest-based authentication), allowsAPI calls to be as fast as possible – a necessity for system-to-system communication.
OAuth1.0a
most secure, signature-based protocolcryptographic signature, (usually HMAC-SHA1) value that combines the token secret, nonce, and other request based information
this level of security comes with a price: generating and validating signatures can be a complex process. You must use specific hashing algorithms with a strict set of steps.
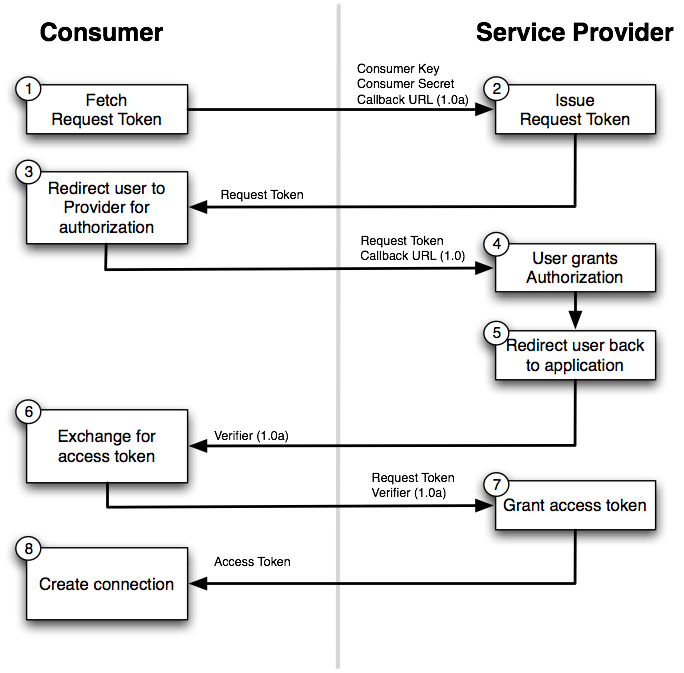
OAuth 1.0a Workflow
Based on having shared secrets between the consumer and the server that are used to calculate signatures. The latter then allow the server to verify the authenticity of API requests.This type of OAuth includes extra steps if compared to OAuth 2.0. It requires that the client ask the server for a request token. This token acts like the authorization code in OAuth 2.0 and is what gets exchanged for the access token.
OAuth 2
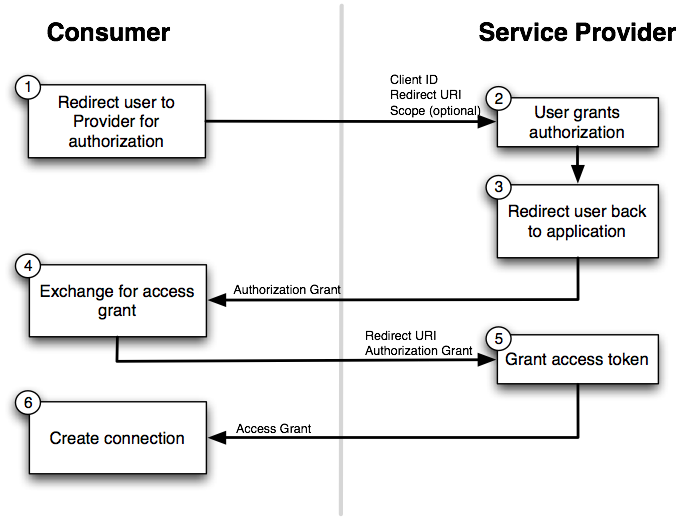
completely different take on authentication that attempts to reduce complexityOAuth3’s current specification removes signatures, so you no longer need to use cryptographic algorithms to create, generate, and validate signatures.v All the encryption is now handled by TLS, which is required
not as many OAuth3 libraries as there are OAuth2a libraries
no digital signature means you can’t verify if contents have been tampered with before or after transit
OAuth2 is recommended over OAuth3 for sensitive data applications. OAuth3 could make sense for less sensitive environments, like some social networks.
OAuth 2 Workflow
OWASP - Top 10 vulnerabilities in online services
https://www.owasp.org/index.php/Category:OWASP_Top_Ten_ProjectOWASP CheatSheets
https://www.owasp.org/index.php/REST_Security_Cheat_Sheethttps://www.owasp.org/index.php/.NET_Security_Cheat_Sheet
My thanks to: https://stormpath.com/blog/secure-your-rest-api-right-way
https://api2cart.com/api-technology/choosing-oauth-type-api/